What is Cyber Security?.
Cyber Security can be defined as Network Security Practices for Protecting Hardware, Software from any damage, alteration of data, or Data Leakage due to Malicious Attacks by a Hacker. Cybersecurity is important because it includes everything related to protecting our confidential data.
- Network Security is important technology to for Protects Computer Networks from Intruders/Hackers. (whether targeted attacks or conditional malware).
- Application/Software Security is basically used to protect any Software or Device from Malicious code or Threats. If an application which is basically installed in your computer or Mobile phone could be used to provide the access to the data to the intruder.
- Information security is Developed for protecting the integrity and privacy of data during any stage of storage and transmission.
- Recovery and Business Continuity after cyber-Attack define how an organization handles cyber security incidents, which cause loss of data. The disaster recovery strategy specifies how the organization restores its operations and information to restore the equivalent operational capabilities before the incident. Business continuity refers to the plan that an organization relies on when trying to operate without certain resources.
- Make User Aware addresses the most unpredictable cybersecurity factor: people. Many People Accidentally install viruses into the computer or network by mistake which causes the failure of any security system. Therefore, Making Users aware of this type of mistake or ignore and delete Suspicious E-mail attachments and websites, also not connect any unrecognized Pen Drives to the system are part of good cyber security practices.
Why Cyber Security is Important in 21st Century ?
You Might be thinking why should I care about cyber security and is it really important for me, then your answer must be yes. Today's generation is completely dependent on Mobile and the internet. Many of us using Mobile phones to store personal data such as videos, Bank account details, Photos, Contact numbers. and, We all installs much application in our phone which may lead to the leak of all these personal information.You might be surprised to know, After installing a malicious application into your phone it could be used as a surveillance device to notice all your movements and many more.
Online Security for Organization or Business
Most organizations are completely relying on IT infrastructure or Computers as the foundation of business processes, and because of this they also need to pay enough attention to IT Security or network security. In 2020, India Reported 1.16 million Cyber Security cases, which is 3 times more than 2019, According to data revealed by the Government of India in Parliament. In India, Almost 3 thousand Online Security related issues were reported every day during the year.In 2019, More than 21K information security breaches were reported in Kazakhstan.
Today, we all need to understand that information and Data are the most valuable assets for any organization, and this also includes very sensitive data of the users. Any compromised online security may lead to data theft, Unauthorized access to organization resources, and malware infection- this all can affect the ability of any business to operate and stand in the market.
So, the, Practices good Cyber Security and making your end user aware of the threat is the only key conditions for ensuring its competitiveness and development.
· As per a report Hackers attack in every 39 seconds, an average of 2,244 times per day Reported by (University of Maryland)
· 8.4 million DDoS attacks were recorded in 2019 (NetScout)
· The average cost of a data breach as of 2019 is $ 3.92 million. (Security Intelligence)
· Since 2019, the number of DDoS attacks has increased by 80%, malware by 35.16%, spam by 26.3%
Types of cyber threats or Cyber Attacks.
We can classify cyber threats into 3 categories.- Cyber crime- which may be induces a group of people performed by an individual, who target or try to obtain personal benefits or cause damage.
- Cyber Attacks- Most of the time after investigating people found Network cyber attacks are done to gathering politically motivated information.
- Cyber Terrorism- It aims or tries to take control over the electronic or digital system of any organization, then destroys it to cause panic or fear
Now Question is, how does a malicious file or virus enter into any system and gain control of it? Here are some common methods used by a different groups of hackers or individuals to threaten network security.
Types of cyber threats or Cyber Attacks
Malware Attack
Malware is also known as Malicious software and it is the Common cyber threat used to gain access to any device. You can understand Malware as software that is basically designed by a Hacker or Cyber Criminal to damage or gain access to the data of any computer user. Most of the time malware is usually spread with the help of email attachments or seemingly downloads from free download websites. This malware software is also used by the cyber criminals to make money or perform politically motivated cyber-attacks.
There are different types of malware for performing online attacks
Virus: Basically it is a self-replicating program, which means it can make its copy that attaches with clean files and spreads through the computer system, most of the time virus encrypted files with malicious codes.
Trojan Horse: It is also a Malicious software that pretends to be legitimate/safe software. Cyber Criminals Used tricks to installing these Trojan Horses to their computers, and gain access to it. For causing any damage or collecting data over the network.
Ransomware: Malicious software used to lock or encrypt users’ files and data. And user needs to pay ransom for decrypting his files or data, if he is denied for ransom the attacker may delete user data.
According to The Indian Express, ransomware attacks worldwide have increased by 102% in 2021 compared to 2020. Ransomware attacks are increasing in number and intensity every passing year.
Adware Malware: It is used to Malicious software. When your computer got affected by adware malware, it starts showing display many unwanted advertisements on your computer. Including Pop-up ads, adult website pages, it will also change your homepage, even your search engine. In simple Add spyware will bombard your display with advertisements and scams.
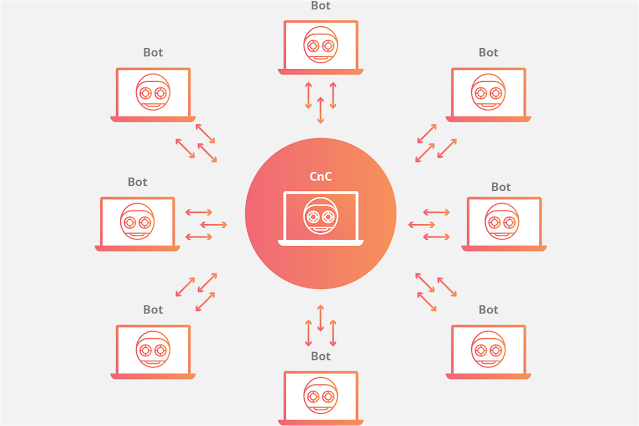
Botnet Malware: This is basically a network that is composed of infected computers from malicious software. Hackers use this malware to perform tasks without the permission of computer users. For Example, Botnet infects any user’s Computer with Malicious software that uses the computer system’s web browsers to divert fraudulent traffic to certain online ads.
SQL Injection Attack: SQL Stands for Structured language query injection, It is a kind of networking attack performed by hackers to gain access and steal database data. Black hat hackers find vulnerabilities in any network application to insert malicious code into the database through malicious SQL statements. After successfully insert code into the database, hackers can access sensitive information in the database.
Phishing Attack: Most Common attack used by hackers or cybercriminals, Such type attacks are used to get someone's Login ID and Passwords, Credit Card Details or other Sensitive credentials. In this attack, a computer user will receive an email for registration, or login, when the user clicks on that link the same website will open which attack is used to steal the information.
Man-in-Middle Attack: in this type of attacks hackers steal data by intercepting communication between two people. For Example, he can easily do this on an unsecured wireless network, or website.
Denial of service attacks is when cyber criminals prevent computer systems from satisfying legitimate requests by overloading the network and servers. This makes the system unusable and prevents an organization from performing important functions.
Cybersecurity advice-protect yourself from cyber attacks
How do companies and individuals guard against cyber threats? The following are our main cybersecurity recommendations:
- Update your software and operating system: This means you will benefit from the latest security patches.
- Use anti-virus software: Security solutions such as Kaspersky Total Security will detect and remove threats. And will keep updating the software to get the best level of protection.
- Use strong passwords: make sure your passwords are not easy to guess.
- Do not open email attachments from unknown senders: these attachments may have been infected by malware.
- Don’t click links in emails from unknown senders or unfamiliar websites: this is a common way to spread malware.
- Avoid using insecure WiFi networks in public places : Insecure networks can make you vulnerable to man-in-the-middle attacks.







1 Comments
Helpful information, keep it up sir
ReplyDelete